We're Streply, a tool that tracks errors and manages logs quickly. It's easy to set up and compatible with many popular frameworks. Made by developers, for developers! If you need to keep an eye on errors and follow logs in your app, create free account.
PHP injection is a method that allows malicious code to be injected into sites that receive user data and have not been properly secured. It is a hacking method that, through personalised code added to, for example, a URL, makes it possible to check configuration files or to perform some operation on a database. An unsecured application is exposed to serious losses, not only in terms of image but also financially.
I invite you to read the article that will explain what PHP injection is, what types of PHP injection there are and how to protect yourself against it.
How PHP Injection Attacks Work
A code injection attack is one of the most popular hacking methods used to inject malicious code or obtain application data. A poorly secured application will allow a hacker to inject a code that would perform some action, such as allowing a hacker to view a configuration file that contains database access data.
Every application, even if it is only accessible to logged-in users, has places that take some value from the user. This could be a form or even a simple URL that contains some variable.
PHP code injection
Code injection is a hacker attack that involves injecting malicious code in order to damage an application, check a code or extract data from, for example, configuration files.
Let's assume that the URL in the application looks like this:
www.aplikacja.pl/profil.php?id=X
where X is the user's unique ID.
Assuming that the application is poorly prepared and the variables are not properly secured, you will probably find something like this in the profile.php file:
$userId = $_GET['id'];
Retrieving the id value from the array of variables $_GET is not secured in any way. The attacker will insert properly prepared code instead of the user ID and the PHP interperator will execute this code as if it were part of the application.
www.aplikacja.pl/profil.php?id=’]; phpinfo();
the above code will display all the information about PHP.
The above example is the simplest and does not pose a threat but you can also call instructions in this way that, for example, will create a file with the content specified for you, e.g. it will display the source of all files on the server.
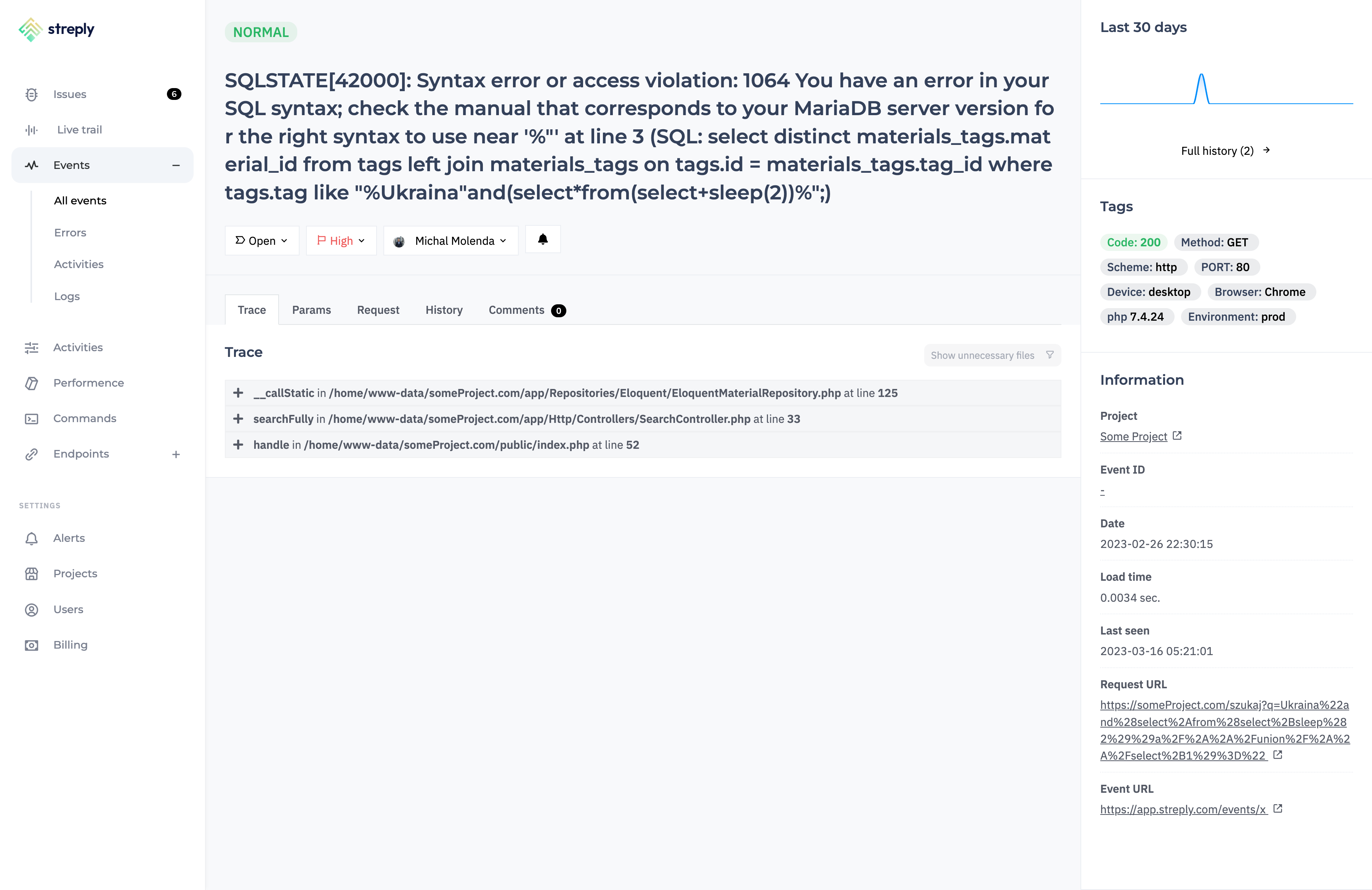
SQL Injection
SQL injection works similar to code injection. The difference is that the code injected into an application is not executed in PHP but directly in the database.
Still operating on the earlier example, we have a file that contains a user ID in the URL:
www.aplikacja.pl/profil.php?id=X
assuming that the code in the file looks like this:
<?php
$userId = $_GET['id'];
…
$user = $this->db->fetch('select * from users where id = ' . $userId);
we have a situation in which we pass a variable to the database query that is not secured and can contain everything.
For example, calling such a URL will delete all the records from the users table:
www.aplikacja.pl/profil.php?id=X; truncate users;
Our id variable is not cleaned up in any way so a query with a code injected in this way will look like this:
select * from users where id = 1; truncate users;
As you can see, the properly injected code made us end this query and immediately add another one which can be very tragic for the application.
Command Injection
Command injection works in the same way as code injection. The difference is that the hacker injects code that calls a function not in PHP but directly on the server.
Assuming we have a code that is supposed to show us a list of all the files uploaded by users based on their ID:
<?php
$userId = $_GET['id'];
…
exec(‘ls -l /storage/’ . $userId);
If you modify the code above, you can, for example, clear all files on the server. All you have to do is modify the URL like this:
www.aplikacja.pl/profil.php?id=1; rm * -Rf /
In addition to getting the list of files using the LS command, we will also call the RM command which is used to delete files. If we will set the root directory, i.e. /, as the parameter, the command would delete all files on the server.
Preventing PHP Code Injections
There are several methods to protect against code injections but the most important is to parse everything the user can pass through the application. All data from URLs and forms must be passed through a function like htmlspecialchars() before they go anywhere further into the application. You must be prepared for the worst-case scenario, i.e. a user trying to intentionally harm your application. You can’t forget any place so it is best to set this type of security globally.
You also need to take care of submitting forms so that someone does not send a crafted request from another site. Such an event is called cross-site request forgery or CSRF in short. You can be protected against this type of situation by adding a token to the form which is then verified after the request is accepted. Frameworks such as Laravel and Symfony have built-in tools that protect against CSRF attacks.
Security in the code is one thing but it is also a very important step to use a tool that will let you know that someone is trying to find a vulnerability in your application. Streply is ideal for this, thanks to its automatic error catching and the logs that can be put on the most important actions of the application you will immediately know when unwanted situations occur.
- We are not pushy
- We only send a few emails every month. That's all.
- No spam
- We only send articles, and helpful tips for developers, not SPAM.
